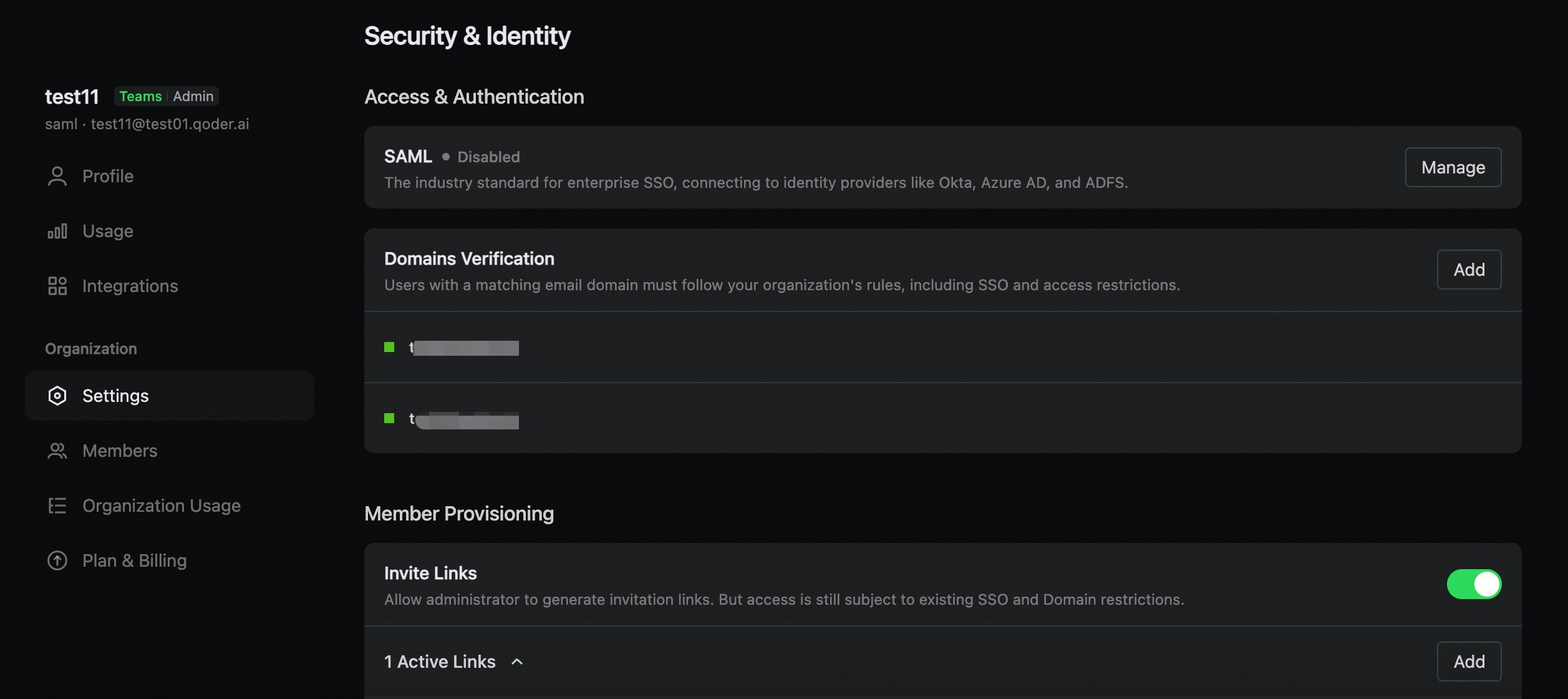
Overview
Security Assertion Markup Language (SAML) 2.0 is an open standard used to exchange authentication and authorization data between an Identity Provider (IDP) and a Service Provider (SP). Once SAML SSO is enabled for your organization, users can authenticate using their corporate Identity Provider without needing to manage separate login credentials.Advantages of SAML SSO
- Enhanced Security: Centralize authentication through your corporate Identity Provider.
- Improved User Experience: A single set of credentials provides access to all corporate applications.
- Simplified User Management: Automated user provisioning.
Prerequisites
Before configuring SAML SSO, please ensure you meet the following requirements:- Admin Permissions: You must have administrative permissions within your organization.
- Identity Provider Permissions: You must have permission to configure applications within your organization’s Identity Provider (IDP).
- DNS Access Permissions: You must have permission to add a TXT record to your organization’s email domain for verification purposes.
Configuration Process
The SAML configuration process consists of the following steps: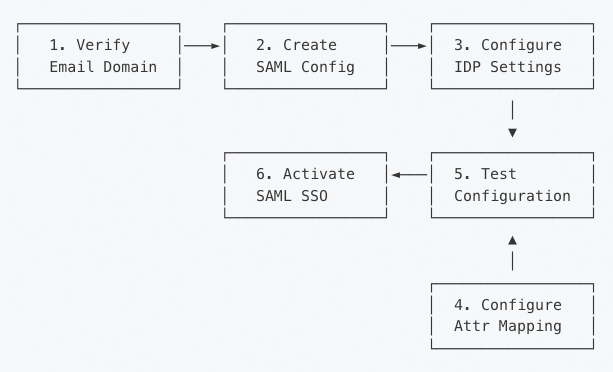
Step 1: Verify Email Domain
Before configuring SAML, you must first verify ownership of your company’s email domain to ensure that only users with an email address from a verified domain can log in through your organization’s SSO. For configuration instructions, see Domain Verification.Step 2: Create SAML Configuration
Create the SAML configuration for your organization. The system will automatically generate the SP certificates and private keys.- Administrators navigate to Organization Settings > Security & Identity.
- Click SAML Configuration.
- SP Entity ID
- SP Metadata URL
- SP ACS (Assertion Consumer Service) URL
- SP certificates and private keys
| Field | Example Value |
|---|---|
| SP Entity ID | https://qoder.com/saml/metadata/{org_id} |
| SP Metadata URL | https://qoder.com/saml/metadata/{org_id} |
| SP ACS URL | https://qoder.com/sso/callback/saml/{org_id} |
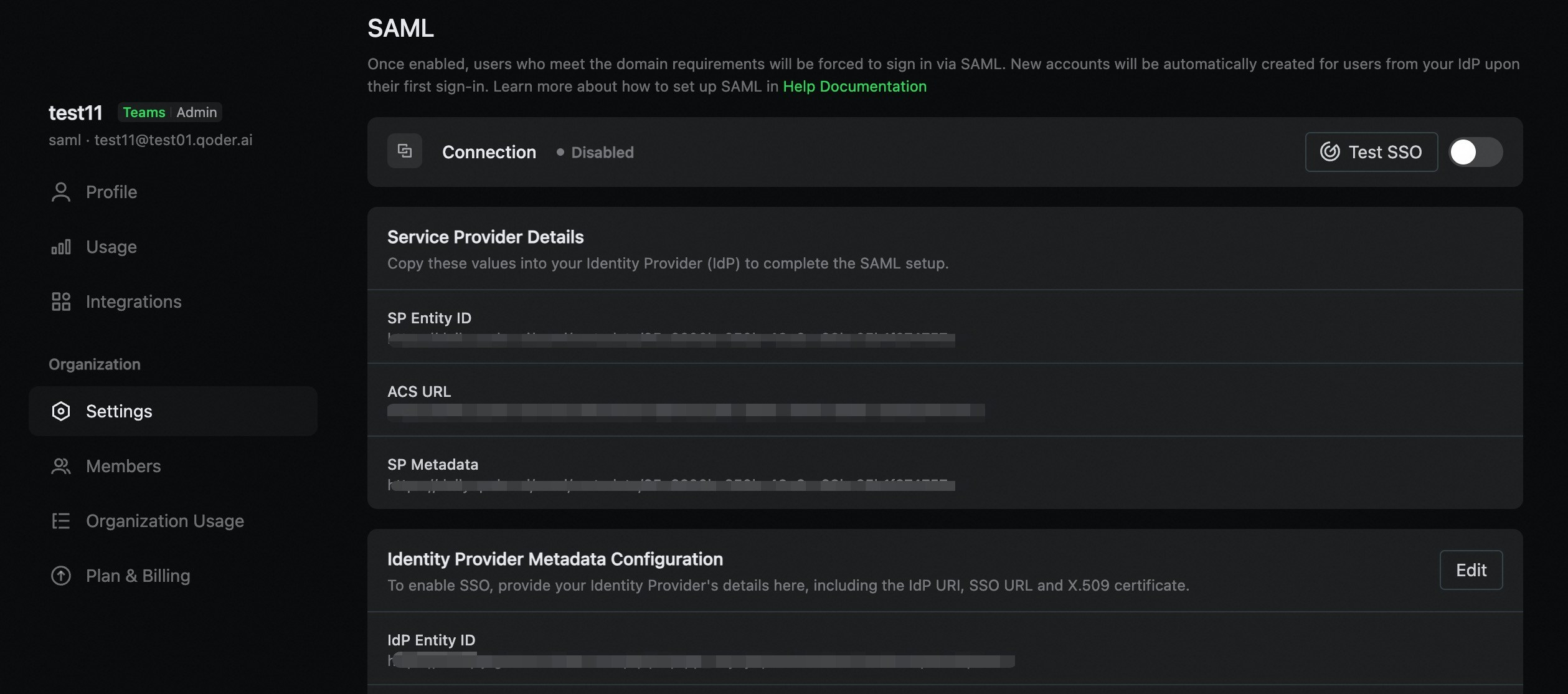
Step 3: Configure Identity Provider (IDP)
You can configure IDP settings using one of two methods:Method A: Automatic Configuration (Recommended)
If your IDP provides a metadata URL, use this method for automatic configuration:- In the SAML Configuration page, locate the Identity Provider Metadata Configuration section.
- Select the Import from URL configuration mode.
- Enter your IDP Metadata URL (e.g.,
https://your-idp.example.com/app/metadata). - Click Save.
- IDP Entity ID
- SSO URL
- Signing certificates
Method B: Manual Configuration
If your IDP doesn’t provide a metadata URL, follow these steps to configure settings manually:- In the SAML Configuration page, select the Manual Configuration mode.
- Fill in the following fields:
- IDP Entity ID: The entity identifier for your identity provider.
- IDP SSO URL: The SSO login endpoint URL.
- IDP Public Certificate: The signing certificate in PEM format (optional but recommended).
- Click Save.
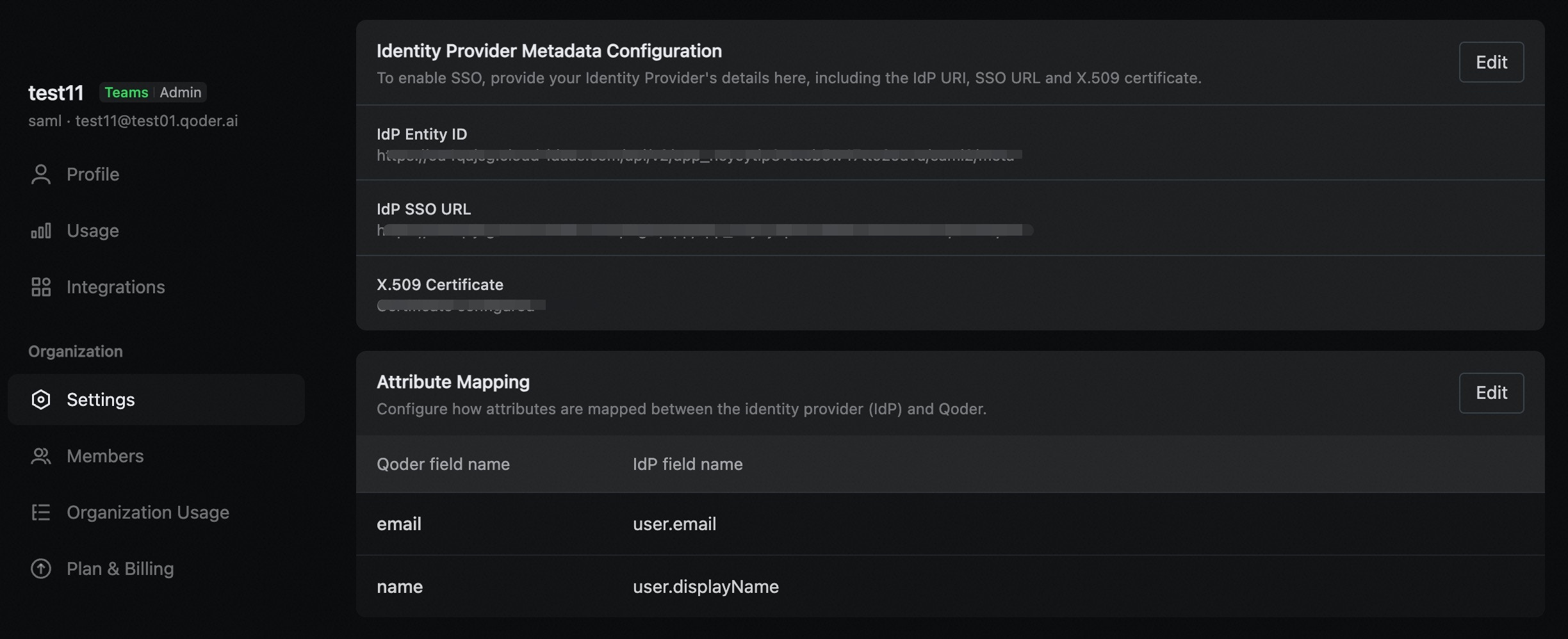
Step 4: Configure Attribute Mapping
SSO supports automatic user provisioning and mapping. You need to configure how user attributes from your Identity Provider (IDP) are mapped to system fields:- In the SAML Configuration page, scroll to the Attribute Mapping section.
- Configure the attribute mappings:
- Email Attribute: The name of the attribute from your IDP for the user’s email address.
- Name Attribute: The name of the attribute for the user’s display name.
- Click Save.
Step 5: Test Configuration
Before activating, test your SAML configuration to ensure all settings are correct:- In the SAML Configuration page, click the Test SSO button.
- The system will run a series of validation checks.
- Review the test results.
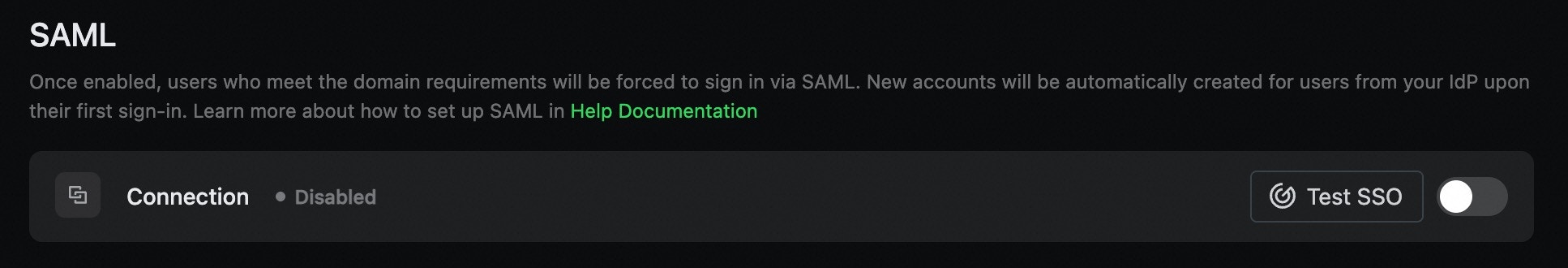
Step 6: Activate SAML
Once testing passes, you can activate SAML SSO:- In the SAML Configuration page, ensure all test checks have passed.
- Click the Enable SSO toggle.
- Confirm the activation in the dialog box that appears.
- The SAML status will change to Active.
- Organization members can now log in using SAML SSO.
- Users with verified email domains will be automatically routed to the SAML SSO login.
Important Recommendation:After activating SAML, the current administrator should not log out immediately. Instead, use a separate user account from a verified domain to test the SSO login and verify the configuration. This ensures that if there is an issue with the SSO setup, the administrator can still access the settings to make adjustments and avoid being locked out.